
Compiled by Americans for Innovation Investigators, Latest rev. Aug. 30, 2018
Findings of Fact, Timeline & Database
The following 1990-2018 timeline and supporting facts provide unmistakable evidence of dereliction of duty, fraud, public corruption, the appearance of impropriety, racketeering, monopoly and anti-trust by senior United States government officials, Harvard, Yale and Stanford academics and alumni, judges, law firms and their commercial accomplices. American patent law itself has been hijacked by these individuals and their organizations.
Alternatively, go to an interactive database library for a list and links to all the files, listed by date and alphabetically, at https://www.fbcoverup.com/docs/library/
Constitutional quiz: What are the -only property rights that the Founders considered important enough to actually write into the Constitution?
Answer: patents and copyrights. (U.S. Constitution, Article I, Section 8, Clause 8.) President George Washington himself signed the first patent, U.S. Patent No. X0000001, on July 31, 1790.
The Founders knew the importance of innovation and invention and created the patent system to protect the young republic’s inventors. They believed patents would grow the economy with new ideas that create new jobs and wealth. But without patent protection, inventors and their investors have no incentive to risk their time and treasure to do the hard work of inventing.
Leader Technologies of Columbus, Ohio, risked 145,000 man-hours over five years with an investment of over $10 million to invent the platform that enables social networking. Leader legally filed for patents that they believed would protect their invention.
But a pattern of public-private corruption—as shown in the following timeline—allowed the well-financed vendor of social networking to steal Leader’s invention, reproduce the design, and then use their ill-gotten gains to perpetuate their crime. They excused their theft by falsely asserting that the technology system was "open source" (i.e., "free") software.
What inventor wants to spend years perfecting and patenting an invention that may then be stolen with impunity? What investor will trust his investment to a government that will not protect the entrepreneurial risk?
When inventors are not rewarded for their inventions, society suffers. China, once known for inventions like paper and fireworks, is now notorious for industrial espionage and intellectual property theft and for copying rather than innovating.
Do we want to risk becoming another China?
To foster the inventive spirit that made America the world’s innovator, we must protect and reward our inventors, and address the corruption that has allowed companies like Leader Technologies, the true inventors of social networking, to be fleeced by the system that was supposed to protect them.
Brief summary of the MANY smoking guns in this collusion:
| Oct. 11, 1996 | False Statements Accountability Act—parties can lie to Congress and courts); |
| Nov. 29, 2001 | IBM forms The Eclipse Foundation |
| Jun. 05, 2002 | Chandler takes custody of Leader's invention source code |
| Aug. 29, 2002 | Leader's invention appears in Eclipse version 2.0.1 |
| Aug. 30, 2002 | Chandler's notes confirm IBM conspiracy to misappropriate Leader's invention |
| Feb. 2-5, 2004 | IBM EclipseCon 2004, Facebook goes live |
| Apr. 12, 2004 | Anne-Marie Slaughter proposed A New World Order |
| Dec. 08, 2004 | IBM"unable to locate" originator of Eclipse code—Leader Technologies |
| Sep. 02, 2008 | A New World Order to "Fundamentally transform America" |
| Sep. 09, 2008 | Eclipse boasts 191 members); Dec. 12, 2008 (FISA court gives Eric Holder dictatorial powers |
| Jun. 06, 2009 | Facebook starts feeding user data to the NSA illegally |
| Jul. 09, 2009 | Sidney Blumenthal writes Facebook into Hillary CFR speech |
| Aug. 03, 2009 | Fenwick & West LLP disclosed Leader as prior art on Andreessen social patents, but not on Zuckerberg patents they filed |
| Apr. 2010 | Zuckerberg refused to provide discovery in Leader v. Facebook |
| Jun. 24, 2010 | Leonard P. Stark shoehorned into Leader v. Facebook 30 days before trial; and Larry Summers' chief of staff, Marne L. Levine went to work for Facebook on the same day |
| Aug. 10, 2010 | Leonard P. Stark confirmed as judge, just two weeks after the Leader v. Facebook trial |
| Feb. 17, 2011 | Obama dines and toasts with Eclipse members in Silicon Valley |
| Jun. 26, 2012 | State Department promoted Facebook use during public litigation that proved Facebook infringes Leader Technologies' patent on 11 of 11 claims and no prior art |
| Jul. 18, 2012 | 28 Zuckerberg hard drives re-discovered! |
| Jun. 06, 2013 | Edward Snowden exposed illegal NSA activity |
| Feb. 08, 2015 | HSBC whistleblower Hervé Falciani exposed Facebook underwriter Deep State |
| Mar. 02, 2015 | Obama met with Technology CEO Council at White House - All "IBM / NSA The Internet of Things" Deep State members |
| Oct. 10, 2015 | Obama made mystery trip to Qualcomm |
| Oct. 12, 2015 | Dell bought EMC - Both Deep State members |
| Dec. 01, 2015 | Zuckerberg announces $45 billion of fraudulent conveyances |
The summary above is not exhaustive, but merely representative of the massive fraud and racketeering that has occurred and continues to occur.
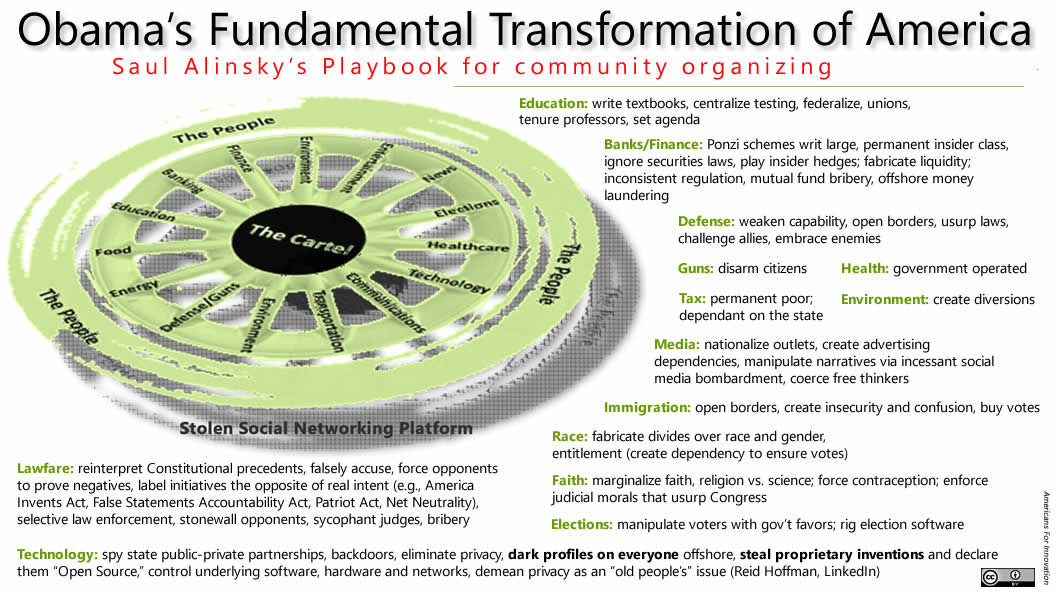
This is the story and timeline of the theft of the invention called "social networking." The thieves are a group we call the "Cartel." and "Deep State." Their motives are ancient. They yearn for money and power. Their goal is a "New World Order." Theft of Columbus, Ohio innovator Leader Technologies' invention enabled them to unify their communications, monitor and control "the masses," and fulfill their rapacious grab for your assets and your liberty.

The U.S. court-proven facts are that Columbus, Ohio innovator, Michael McKibben, and the company he founded, Leader Technologies, invented social networking in the late 1990’s. Prior to that, McKibben had re-built AT&T’s email system in record time for release with Microsoft’s much ballyhooed Windows 95.
In 6, Leader was awarded its first patent. However, once the Deep State learned about Leader’s invention from an unscrupulous patent attorney and adviser to IBM and the NSA, they wanted it so badly they broke many laws to get it. The invention enabled them to create "The Internet of Things" or "The Internet of Everything" where they could permanently control the digital economy in all its aspects: communications, banking, law, energy, finance, elections, defense, technology, communications, media, healthcare, education, entertainment, politics, guns, food, environment and news.
This sounds like Hollywood fiction, but as you will read in these pages, it is all too real.
The roots of the modern day "One World Order" agenda go back to the 1700’s and philosopher Emmanuel Kant’s essay. In the 20th century, President Woodrow Wilson’s failed effort to form The League of Nations eventually became The United Nations. The disciples of this soulless, mechanistic agenda include George Soros, Bilderberg Group, the 1910 Jekyll Island Club duck-hunt, World Economic Forum (Davos), Council on Foreign Relations, Wall Street, Silicon Valley, and a slew of politicians, judges and bureaucrats. They benefit personally through investment gains and insider information.
World government is the notion of a common political authority for all of humanity, yielding a global government and a single state. Such a government could come into existence either through violent and compulsory world domination or through peaceful and voluntary supranational union. In such a world, national constitutions must be subservient to the single state.
Proponents of A New World Order are betting against America
On Jan. 05, 2011, new world order godfather and post-WWII Hungarian immigrant to America, George Soros (György Schwartz), stated that the "new world order" will be a healthy, if painful [violent] adjustment." He continued, "China will be the 'engine driving it forward and the U.S. will be actually a drag that is being pulled along through a gradual decline in the dollar.'"[294]
Education or Propaganda? The minds of our youth are targeted
Nowhere is more telling of the Deep State’s agenda than the uproar over Common Core. Critical to the Deep State agenda is the centralized control of education via Common Core in secondary education and M.O.O.C. (Massive Open Online Course) in higher education. Just like the re-education camps of every totalitarian ideology before them (like Mao, Lenin, Pol Pot, Stalin, Hitler, Brownshirts, Komsomol), the Deep State works to control the "narratives" that our children learn.
Where the facts do not fit the Deep State narrative, the facts are ignored or altered. They want to grow obedient, docile, faithless worker bees for their factories. Just like George Orwell envisioned in 1984, gone will be free thinking, free will and individuality. Liberty will be replaced by oligarchies, a permanent under-class, doublespeak, political correctness, disrespect, reading between the lines, hate, intolerance, inequality and brutality.
The digital part of this remaking of education is well down the path. Most secondary schools use Google Docs almost exclusively for their document sharing. In universities, M.O.O.C. curricula are rapidly replacing individualized instruction in favor of the allegedly more "rich" (cleansed and censored) content of "Big Data" and "The Cloud."
Universities are being connected using The Ohio State University's IBM / Microsoft / Oracle / SAP / Eclipse data center as an international M.O.O.C. network hub that Presidential candidate John Kasich approved. The supply of Deep State shiny things to lure educators, parents and students into this morally dark world appears unstoppable as the "users" mainline on the digital drugs.
This Leader v. Facebook timeline (below) reveals Deep State names, places and illegal acts
Hillary Clinton’s political adviser, Anne-Marie Slaughter (2009-2013) implemented her book—A New World Order (Princeton Press 2004)—when she worked for Hillary at the State Department. She started promoting Facebook at the State Department in 2009, even though Facebook did not have the intellectual property rights. Of note, Slaughter has Hungarian immigrant connections by marriage with Soros, Intel’s Andy Grove and IDG-Accel Partners (China)’s John P. Breyer. Accel is Facebook’s 2nd largest shareholder.
Bookmark: #saul-alinskyLying is a Saul D. Alinsky tactic (and also permitted in the Koran when Muslims are dealing with Westerners, Christians and Jews—Qur'an 3:28)
To gain control of the world’s information (and thus its money and power), the Deep State employs the political organizing tactics of Saul D. Alinsky. Hillary Clinton is an expert. She wrote her undergraduate thesis on Alinsky and corresponded with him.[299] Barack Obama employs Alinsky’s bible—12 Rules for Radicals (Random House 1971).
Tellingly, Alinsky dedicated 12 Rules to Lucifer, who he calls the original radical. Lucifer is one of the names for Satan, the Devil, the Evil One and The Dragon (The Book of Revelations 12: 2; 20:2).
The Obamas and Clintons employ Alinksy’s habitual lying technique: Keep the enemy confused and on its heels working to keep up with your lies. Lies also often become truths if repeated incessantly. For example, the lies about Zuckerberg and Facebook in The Social Network movie are accepted as the truth by many.
In the movie and in sworn testimony, Zuckerberg claimed to have invented Facebook in a few weeks, while preparing for finals at Harvard, and drinking. Contrast that with the 145,000 person-hours and over $10 million spent by Leader Technologies. Zuckerberg's assertion is totally illogical, yet it persists.
Obama’s and Hillary’s lies are legion. Their whoppers include: (1) Obama’s oft-repeated promise "If you like your doctor, you can keep your doctor," (2) Obama’s claim to be a Christian to fool voters, (3) Hillary’s fabrication that a video caused the attack on the U. S. Embassy in Benghazi, and (4) Hillary’s ever-changing private email stories which are being investigated by the FBI, with new evidence proving she exposed the highest classifications of intelligence.
They have also brazenly ignored and violated laws. They encourage others to violate U.S. laws themselves, and not respect traditional authority—our borders, the U.S. Constitution and the people responsible for carrying out our laws, such as our police and military personnel. The Justice Department's U.S. Attorneys have become little more than mobsters themselves—A fish rots from the head down.
The Deep State’s corrupt tactics in Leader v. Facebook were purposely confusing in order to discourage the public from learning the truth
The following timeline is complex. That is an Alinsky tactic: Put so many layers of lies on the onion that most people won’t take the time to peel them away.
Americans for Innovation has been peeling away the layers of this Leader v. Facebook judicial corruption onion for years. The Deep State’s onion core is now exposed. Names, places, dates, crimes and motives have been uncovered thanks to the dedicated work of many.
Soros’ New World Order wants to force its will on America and the planet. In their morality, you would be reduced to merely a consuming animal—"a useful idiot" (Alinsky). In their world, faith, hope and love are the antiquated values of weak people. They also have little need for any constitution, law or regulation that stands in their way.
* Alinsky used the phrase "a useful idiot" is sometimes attributed to Vladimir Lenin, although this is in question.
Lure users, young and old, into "The Cloud," then ambush them
Theft of Leader Technologies’ invention of social networking was critical to the Deep State’s plan. With control of the digital essences of our lives ("The Internet of Things" aka "The Cloud"), the Deep State could achieve their new world order more quickly.
Which side are you on?
The moral, philosophical and cultural battle lines are drawn. If we choose the globalist Cartel, the "nanny state" of entitlements will eventually overtake us like it collapsed the Soviet Union. On the other hand, if we choose the timeless values of the U.S. Constitution, we must protect and restore Leader Technologies’ property rights. Then, we empower real, ethical innovators to rebuild our digital networks in a way that takes us to higher ground.
In our increasingly global economy, the U.S. has a major advantage—our inventiveness and entrepreneurial spirit. But we are allowing our advantage to evaporate. If someone had backed up a truck to the "back door" of the U.S. and stolen trillions of dollars worth of property, we would be Carteloutraged and more protective in the future. This is exactly what has happened over the past few years—yet there is no defensive uproar. We cannot allow this thievery to continue.
This restoration of Leader Technologies’ (and others) property rights will expose the decades of corruption that has resulted in this digital takeover. Whether these criminals go to jail, are pardoned or ignored, one thing is for sure-- they must be defunded and disempowered.
Is "the New World Order" too big to fail?
Some ask if social networks are now "too big to fail." The last time Americans thought that was when our too-big-to-fail banks were bailed out in 2008. The taxpayer was stuck with the bill while the bankers continued to pay themselves bonuses. Not a single banker was jailed, fired or even fined. Is this the New World Order we have to look forward to? The answer is yes, unless WE THE PEOPLE put a stop to this profligacy.
These social networks can and will be reconfigured to provide the positive benefits without the abuses of security and privacy. However, they will not be run by the current crop of "public-private" criminals, who must be run out of town, this current President and his cabinet among them.
Read on.
In the dramatic up tick in White House polemics about Islam, it becomes important to note that unlike Christianity and Judaism where lying is a sin, Muslims are permitted to lie to Westerners, Jews and Christians. Qur'an 3:28.

Barack Obama's hollow claims of Christian faith, and his embrace of Islam in the White House, would certainly explain why his administration lies without shame to achieve its Slaughter-esque disaggregation goals.
This disaggregation governance philosophy was introduced by Anne-Marie Slaughter to the U.S. State Department on Apr. 12, 2004. She was then a Princeton international law professor and had just published her book, A New World Order (Princeton University Press 2004). In 2009, she served as a chief political advisor to Secretary of State Hillary Clinton (2009-2013).[276]
In evident excitement about the coming presidency of Barack Obama, Princeton re-published the book (never mind that the 2008 election was still two months away). Slaughter's ideas have provided a suitably academic rationale for the institutionalization of crony capitalism and the establishment of a permanent power class for those deemed worthy of an invitation to the networking party ("The Cartel" or "Deep State").
The Deep State needed a global technology platform, so they stole Columbus, Ohio innovator Leader Technologies' invention of social networking. Leader's invention overcame inherent "scalability" problems the Deep State was having with legacy IBM, Microsoft and Xerox client-server platforms.
IBM pumped in a $40 million "donation" to The Eclipse Foundation. Leader's patent attorney, James P. Chandler, III (who was also counsel to IBM), secretly fed Leader's invention to Eclipse. Then a Who's Who of companies like SAP, Borland, Cisco, Intel, Oracle, Wind River, Nokia, HP and Microsoft signed up to get Leader's invention at a breathtaking rate.
Leader's invention enabled Eclipse members to unify their "disaggregation" networking efforts around the planet. In his hubris, Harvard Law professor James P. Chandler described his theft of his client's invention for the Deep State as "in the greater good."
A world of interdependent, self-regulating international networks where the U.S. Constitution is in the way
Tellingly, Slaughter never mentions the U.S. Constitution as a guiding principle in her speech introducing A New World Order to the State Department on Apr. 12, 2004. Neither does she mention Leader Technologies on whom she and her cronies rely to pull off their heist.[285]
* * *
"[C]ourts should not make policy or invent rights not stipulated or implied by statutes or the Constitution's text. But courts have no nobler function than that of actively defending property, contracts and other bulwarks of freedom against depredations by government, including by popularly elected, and popular, officials." —George F. Will[001]
"The banking powers are more despotic than a monarchy, more insolent than autocracy, more selfish than bureaucracy."—Abraham Lincoln (1863)
"Those who would give up essential liberty to purchase a little temporary safety, deserve neither liberty nor safety."—Benjamin Franklin (1789)


(a) Knowledge of egregious denial of due process to Leader,[007]
(b) Multiple notices of the emergence of 28 previously concealed Zuckerberg computer hard drives and Harvard emails; Facebook’s attorney Gibson Dunn LLP[008] (who concealed them) was representing Facebook in the case;[009]
(c) Substantial financial conflicts of interest by the judges and government officials[010] involved in this case, e.g., holdings in Fidelity[011] Contrafund,[840] Vanguard[013] and T. Rowe Price[014]—who are among the largest and notorious pre-IPO mutual fund investors in Facebook, and
(d) Substantial relationship conflicts of interest among the judges with Gibson Dunn LLP, various other Facebook attorneys, including Cooley Godward LLP,[015] Facebook investors, Leader potential witnesses, the Patent Office and other U.S. government officials and advisers.[016]
How many Harvard, Stanford and Yale graduates does it take to corrupt global technology, commerce and government? At least four years of investigations conclude: Sixty-five (65) from Harvard, fifteen (15) from Stanford and seventeen (17) from Yale.
Here is the Gallery in alphabetical order:
Bookmark: #Fig-11Bookmark: #cia-formed Bookmark: #1947
| Atlantic Council Directors (2014) include:[1036] | ||
| Lastname | Firstname | SES Member* |
| Acheson | David C. | Yes |
| Albright | Madeleine J.K. | Yes |
| Bagley | Elizabeth F. | Yes |
| Baker, III | James A. | Yes |
| Brown | Harold | Yes |
| Carlucci, III | Frank C. | Yes |
| Clark | Wesley K. | Yes |
| Dodd | Christopher J. | |
| Egan, Jr | Thomas J. | |
| Gates | Robert M. | Yes |
| Hayden | Michael V. | Yes |
| Kissinger | Henry A. | |
| Mullen | Michael G. | |
| Perry | William J. | Yes |
| Pickering | Thomas R. | Yes |
| Powell | Colin L. | Yes |
| Rice | Condoleezza | Yes |
| Rowny | Edward L. | Yes |
| Shultz | George P. | Yes |
| Slaughter | Anne-Marie | |
| Taft, IV | William H. | |
| Verveer | Melanne | Yes |
| Warner | John W. | |
| Webster | William H. | Yes |
| Woolsey Jr. | R. James | |
Bookmark: #kennedy-assassinated Bookmark: #1963
JFK: “. . . to splinter the C.I.A. in thousand pieces and scatter it to the winds.” New York Times[833]
Bookmark: #church-committee-hearings Bookmark: #1976
| 1980 Plum Book includes:[1036] | ||
| No. | Lastname | Firstname |
| 1 | Babbitt | Bruce |
| 2 | Bradley | Thomas |
| 3 | Bremer | L. Paul |
| 4 | Brzezinski | Zbigniew K. |
| 5 | Bundy | McGeorge |
| 6 | Carlucci | Frank C. |
| 7 | Holbrooke | Richard |
| 8 | Kennedy | Patrick F. |
| 9 | Lake | William T. |
| 10 | Marshall | Andrew W. |
| 11 | Muskie | Edmund S. |
| 12 | Pickering | Thomas R. |
| 13 | Rockefeller | Sharon P. |
| 14 | Scowcroft | Brent |
| 15 | Volcker | Paul A. |
| 16 | Warren | Christopher |
| 17 | Watson, Jr. | Thomas J. (IBM - Moscow) |
| 1984 Plum Book includes:[1035] | ||
| No. | Lastname | Firstname |
| 1 | Armitage | Richard K. |
| 2 | Ayer | Donald B. |
| 3 | Baker III | James A. |
| 4 | Balridge | Malcolm |
| 5 | Bork | Robert H. |
| 6 | Breyer | Stephen G. |
| 7 | DiGenova | Joseph E. |
| 8 | Farnan, Jr. | Joseph J. |
| 9 | Ginsburg | Ruth Bader |
| 10 | Jackson | Thomas Penfield |
| 11 | Marshall | Andrew W. |
| 12 | Meese III | Edwin |
| 13 | Olson | Theodore B. |
| 14 | Orrick Jr. | William H. |
| 15 | Scalia | Antonin |
| 16 | Sessions III | Jefferson B. |
| 17 | Starr | Kenneth W. |
| 18 | Taft IV | William H. |
| 19 | Webb | Dan K. |
| 20 | Weinberger | Casper W. |
Bookmark: #shadowy-government Bookmark: #1987
"There exists a shadowy Government with its own Air Force, its own Navy, its own fundraising mechanism, and the ability to pursue its own ideas of the national interest, free from all checks and balances, and free from the law itself."
| 1988 Plum Book includes:[1035] | ||
| No. | Lastname | Firstname |
| 1 | Armitage | Richard K. |
| 2 | Ayer | Donald B. |
| 3 | Baker III | James A. |
| 4 | Balridge | Malcolm |
| 5 | Bork | Robert H. |
| 6 | Breyer | Stephen G. |
| 7 | DiGenova | Joseph E. |
| 8 | Farnan, Jr.* | Joseph J. |
| 9 | Ginsburg | Ruth Bader |
| 10 | Jackson | Thomas Penfield |
| 11 | Marshall | Andrew W. |
| 12 | Meese III | Edwin |
| 13 | Olson | Theodore B. |
| 14 | Orrick Jr. | William H. |
| 15 | Scalia | Antonin |
| 16 | Sessions III | Jefferson B. |
| 17 | Starr | Kenneth W. |
| 18 | Taft IV | William H. |
| 19 | Webb | Dan K. |
| 20 | Weinberger | Casper W. |
| * Judge Joseph J. Farnan was the first trial lawyer who devastated Facebook at the Markman Hearing of Leader v. Faebook. He was replaced just one month before trial by Obama nominee Leonard P. Stark just one month before trial, after which Stark allowed Facebook to completely change its claims and barred Leader from additional discovery in an evident abuse of due process. | ||
Bookmark: #rise-of-spy-state-oligarchy Bookmark: #1990
A "public-private" plan to privatize the management of American security and intelligence appears to have hatched from this Chandler-Freeze association in the early 1990's.
On Jun. 07, 1993—five months into Bill Clinton's first term as President in 1993—Clinton advisors James P. Chandler and John D. Podesta hosted an encryption conference in Washington, D.C.
The clear objective of that conference was to create a rationale to give Clinton's Deep State intelligence people a universal backdoor key to all digital communications.
During 1993-1994, Bill & Hillary Clinton's political enemies were being killed of like flies, as revealed by their long term Arkansas political "fixer," Larry Nichols, producer of The Clinton Chronicles (1994).
Tellingly, on Apr.
17, 1995, Bill Clinton signed Executive Order No. 12958[271] Classified National Security (first published on Jan. 01, 1995). This order appears to be the legal genesis for an illegal Deep C.I.A. Spy State run out of the White House used to gather dirt on individuals across the planet. Chandler very evidently wrote this executive order and provided the continuity for this illegal agency through the Clinton, Bush and Obama presidencies.
During this time, Chandler and Freeze privately formed and repeatedly flipped a company named Eurotech, Ltd. that supplies software and hardware to the spy state. A decade later, they both served as directors for Columbus innovator, Leader Technologies, until that is, Chandler took custody of a copy of Leader's source code on June 05, 2002 and that code then magically appeared in the "open source" programming code of the IBM Eclipse Foundation just 11 weeks later.
Leader Technologies invention was social networking (which these spy state aficionados clearly wanted for their schemes). It solved a "scalability" problem that Microsoft's, IBM's and Xerox's older client-server architectures were choking on.
Leader's innovations were sent immediately to Chandler's long-time crony client and technology supplier to the secret Deep State—IBM, where the future Patent Office director David J. Kappos was waiting for it. As just stated, eleven weeks later, Leader's innovations first appeared in IBM's Eclipse Foundation release 2.0.1 with illegal IBM copyright claims. Eighteen months later, with Larry Summers now its president, Facebook emerged at Harvard. Facebook was just the first of numerous NSA data gathering fronts to emerge from IBM Eclipse, a ring leader in this scheme.
It would be macabre if their choice of "The Eclipse Foundation" name alluded to the damage done by their in-your-face eclipse of the U.S. Constitution.

Behind this national security smokescreen (it's for the greater good), these men concocted a legal sophistry that lured American citizens into agreeing to give away their sacred Constitutional rights to privacy in exchange for "free" online services.
With these "end user license agreements" in hand, the NSA was given the legal clearance to spy on Americans. Much, if not most, of this legal vision is the brainchild of James P. Chandler, who now operates a fifth column within the Obama Administration, probably even vetting all FOIA requests for the White House.
Chandler is the author of the Economic Espionage Act of 1996 under Bill Clinton. One of Bill Clinton's last acts as president was to appoint Chandler to the National Infrastructure Assurance Council ("NIAC") just two days before he left office on Jan. 20, 2001.[024] Chandler directed ongoing traffic for this spy state agenda, starting under Clinton, through Bush, and now under Obama.
To facilitate the "Big Data" collection, these three presidential administrations cleared the regulatory path ways for Wall Street and Silicon Valley to form companies to give the illusion of choice—but don't be fooled, they are all NSA "old boy" creations.
Indeed, Washington, D.C. insiders report that a central actor in this corruption, Clinton security adviser James P. Chandler, has famously declared that the "prime" defense contractors (Boeing, Lockheed, Northrop Grumman, General Dynamics and Raytheon) are merely revolving door agencies of the federal government. Chandler has merely extended his philosophy of an insider's game to the control of the Internet, exhibited by the NSA's abuse of privacy.
The legislative, executive, judicial and Free Press institutions of our Republic stopped working as designed
The quid pro quo for American intelligence under the Executive branch was that these private companies would feed funds and data to the NSA and government insiders without Congressional approval (the Legislative branch). Blackmail, extortion, intimidation and coercion by insiders is inescapable. It is just what bad people do.
The quid pro quo for the cooperation of the Judicial branch was new wealth from specially organized Wall Street mutual funds and waiver of judicial ethics rules that would look the other way when these mutual funds were disclosed. What judge or judicial employee will resist the tipsters subsequently?
The quid pro quo for the Free Press was income from advertising and voter manipulation. In exchange, the "lame stream media" stopped holding the powerful accountable because the Silicon Valley purveyors of "Big Data" and their bankers fed them advertising. They have become data junkies. Sadly, the press began using the unverified "narratives" of the spy state conspirators as their primary sources, thus reinforcing the lies. The Social Network is a perfect example of a lying "narrative" about Mark Zuckerberg and Facebook that the public believed because the mainstream media never questioned its veracity.
Constitutional checks and balances have degenerated into competing oligarchies and secret alliances
In short, this "public-private partnership" scheme pressed by Hillary Clinton adviser, Anne-Marie Slaughter ("A New World Order"), has destroyed Constitutional checks and balances. In its place are unaccountable spy state oligarchies based on ill-conceived and self-serving "international networks."


''This is an historic moment. We have in this past year made great progress in ending the long era of conflict and cold war. We have before us the opportunity to forge for ourselves and for future generations a new world order — a world where the rule of law, not the law of the jungle, governs the conduct of nations. When we are successful — and we will be — we have a real chance at this new world order, an order in which a credible United Nations can use its peacekeeping role to fulfill the promise and vision of the U.N.'s founders."